Napolitano: FBI Plan to Access Browser History “Major Step Towards Police State”
The Latest news as it relates to the emerging Police State
It never gets better no matter who is in the White House, he said
However, the FBI is able to bypass the court system and access information relating to an individual’s phone records through the use of a “National Security Letter.”
“NSLs are shadowy administrative subpoenas for information issued by the FBI, whose authority to use them was bolstered by the Patriot Act in 2001,” as reported by US News and World Report. “The requests often are accompanied by a gag order disallowing the company from which information is sought from discussing it.”
FBI Director James B. Comey has requested Congress pass legislation to amend a “typo” in the Electronic Communications Privacy Act that, he claims, has allowed some tech companies to refuse to provide data that Congress originally intended them to hand over to the FBI.
The new legislation, if passed, would allow the FBI to access an individual’s browser history by using a National Security Letter, rather than a warrant from the FISA Court. A National Security Letter only requires approval from the special agent in charge of a FBI Field Office.
Appearing before the Senate Intelligence Committee in February, Comey claimed the inability to obtain electronic information without a NSL affects the FBI’s work, “in a very, very big and practical way.” The Intelligence Authorization Act of 2017, with the NSL amendment attached, will now head to the full Senate for a vote.
Senator Ron Wyden (D-Ore.) was the sole member of the Intelligence Committee in opposition to the amendment.
“This bill takes a hatchet to important protections for Americans’ liberty,” he said. “This bill would mean more government surveillance of Americans, less due process, and less independent oversight of US intelligence agencies.”
Texas Republican Senator John Cornyn is a co-sponsor of a similar amendment that is set to be voted on by the Senate Judiciary Committee on Thursday; He has argued a “scrivener’s error” in the law is “needlessly hamstringing our counterintelligence and counterterrorism efforts.”
A coalition of tech firms and privacy advocates submitted a letter to the members of the Senate Judiciary Committee expressing concern over the amendment and the threat it poses to civil liberties.
“This expansion of the NSL statute has been characterized by some government officials as merely fixing a ‘typo’ in the law,” they wrote. In reality, however, it would dramatically expand the ability of the FBI to get sensitive information about users’ online activities without court oversight.”
Appearing with Shepard Smith on Fox News, Judge Andrew Napolitano expressed anger over the amendment and warned the American people to wake up to the ongoing erosion of their civil liberties.
“It gets worse, it never gets better no matter who is in the White House, no matter which party controls the Congress,” he said. “The American people should wake up….This is a major step towards a police state.”
“It’s done in the name of, it’s always done in the name of keeping us safe. Who or what will keep our liberties safe?”
Big Brother 2016: Beyond Orwell's wildest dreams
Media is doling out in bite-sized bits what we already knew: we are being tracked and traced, recorded and stored.
The Guardian recently told us that – shock – Google is storing lots of information about us; meanwhile, the wildly different Independent gently awakens us
to the fact that Facebook is doing something almost identical. Both
articles contain instructions on how to appear to thwart these
intrusions.Oh well, click, click, yawn. Safe again.
An Orwellian present
Most people who read my column will have read Orwell’s 1984. And most who haven’t will have seen the film (the one with John Hurt, I hope). If you haven’t done either, go and do one of them right now.Orwell’s famous dystopian vision describes a world in which the State knows everything about you. He had entitled his book The Last Man – meaning by that: The last true man left on earth. It was changed – perhaps fortuitously – by the publisher.
The book fed a slew of references into the culture, seemingly understood even by those who had never read it: Big Brother, Doublespeak, Sex Crime, Winston Smith.
The world Winston inhabits is physically viler and more obviously brutal that ours – at least if you live outside the perimeters of the wars the US is waging directly or indirectly. Its architecture and ambiance are, likewise, orders of magnitude darker and more depressing than ours – parts of inner cities excepted.
Orwell’s Doublespeak is more directly relevant to our experience today. With things now routinely called by something other than their proper names – men ‘identifying’ as women, women ‘identifying’ as men, men ‘identifying’ as dogs, and forty-six-year-old fathers ‘identifying’ as six-year-old girls – our world is littered with an increasing number of obvious truths which must be resolutely ignored on the grounds of political necessity.
Doublespeak has hamstrung academia – rendering whole swathes of it inoperative, and much of the rest of it either irrelevant, farcical or pernicious.
In our day-to-day exchanges it has resulted in smile-fronted loneliness and lurking suspicion as necessary features of a life wherein those of us who comment openly upon the Spandex-coated bars of our prison are treated as pariahs and lepers.
As in Orwell’s world, our language is undergoing a thinning process and morphing into a ghettoized Newspeak and Twitteresque literary shorthand. Our grandparents knew what it was to speak and write well because they acknowledged an objective standard. Those who attained it were regarded as exemplars, and those who had not could see what remained to be done. Now, as in so much else, mediocrity and approximation are defended as acceptable standards; simply noticing one’s own shortcomings is elitist – and, therefore, contemptible – while commenting on another’s is an outright sin.
The result is a common language attenuated to the point where being correctly understood is increasingly difficult, and the scope for being wrongfully construed almost unlimited.
But here the overlap in terms of content between our world and Orwell’s thins out in favor of a stark – and for some disarming – stylistic dissonance.
Orwell’s world is bleak. It is dark. The walls are covered – at best – by poorly applied institutional paint and creeping mold. The lights hang by a rat-eaten wire and flicker erratically, serving only – to plunder Milton – to discover sights of woe, regions of sorrow, doleful shades. Orwell’s “boot stamping on a human face – forever” is congruent in Hollywood terms with the scenery.
But our world is not like that. At least, not yet. Much of it is shiny and manicured – and not only for the technocrats and Inner Party members, but also for the drones of the Outer Party like Winston Smith.
Today, Smith does not wear dungarees and inhabit cold, dark corners creeping with vermin. He wears clothes which look something like what he sees on TV. He makes his car repayments. True, what he buys has the obsolescence of Orwell’s world, but that is due to a design philosophy geared to keep the drones shopping, rather than a simple inability to produce at all.
These seeming contradictions are difficult to process. A system which tortures you and stamps on your face might still be identified by the proles in their current state of conditioning as an enemy. But boot-stamping is not our experience – again, at least not yet.
The Big Brother of our experience has a public relations department and a team of designers with bed-head haircuts working on more palatable and fabulous ways to sell you servitude. Our prison does not simply consist of bars. It consists of hi-tech, ergonomically designed, ambient-adjustable bars. And it is policed by people who want you to call them by their first name; who are trained to seem to agree with you; who sit patiently when you talk, and then tell you to have a nice day.
If this seems unconnected with your current worldview, consider that some of the highest-profile puppets we vote for recently attended the opening of the Gotthard Tunnel, Switzerland – without batting an eyelid.
Online 1984
Our online experience broadly resembles our offline experience.Sure, if you are deep in the bowels of Badnet – downloading a program you just discovered you really need but don’t want to pay for from a site featuring languages you don’t understand and from which windows with images of scantily dressed females jump out erratically at you – then you expect nasties. It feels dodgy and dangerous – and it is.
But Facebook and Google don’t feel like that. They are shiny, convenient heavens generated by serried ranks of earnest, enthusiastic angels in love with what they do. They love you, too. They don’t love you individually, but they love you mathematically; they love you when enough of you say the same thing to them for it to be incrementally advantageous to do something about your prayers. The world they produce feels professional and safe, something like a cross between a business park, a shopping mall where everything is free, and a children’s nursery.
This does not feel like a place where boots stamp on faces forever.
Collecting data
A common misconception about this ergonomic, customer-service Big Brother decked out in primary colors is that he couldn’t possibly watch everyone at the time.But it doesn’t work like that. Mostly, he doesn’t care what you are doing on a day-to-day basis.
When databases were created in the 1970s, storing stuff was very expensive. That’s why they used the relational data model: it could cram more stuff into less space.
Now storing stuff costs nothing. I bought a 16 GB USB memory stick for the price of two cups of coffee last week. So they are not watching you. They are storing what you do.
Firstly, in case they need it. As morals, mores and norms are re-engineered and hemorrhage and coalesce in new configurations and are downloaded as normative updates by a population unable to concentrate or remember, everyone eventually will be a criminal – at least retrospectively. There is no future-proofing compliance with this new system of control. No matter how quickly you take the upgrades in Newthink, proof of your Oldthink will be accessible and visible to those who care to use it against you.
Secondly, they are building profiles. They want to know who the troublemakers are.
Those at the helm couldn’t care less what you think currently. If you are intelligent and happen to have spent your time online researching rather than looking at compilations of top goal-scoring moments, pornography, or highly pixelated editions of the Simpsons’ back catalog, that is likely to have rendered you a social outcast sheltering under the bridge of your own Cassandra complex yelling at random passing cars. So they don’t care about you – at least, not yet.
What they are on the lookout for in the current phase is a rogue idea. They are afraid that some bright individual will find the solar plexus of the psychological control grid and start jumping up and down on it. And they are also making sure existing powerful entities don’t go off the reservation of what is agreed by the guiding think tanks and conclaves of the mighty.
What to do?
We incline toward fight or flight. Many feel their security lies in keeping their heads down, by conforming. While I understand the feeling, my opinion is that no amount of conformity will be enough to placate what is coming. This system does not simply want conformity – although it does require it – it will not rest until it has your homage. For myself, my mind is made up: I will not bow to the new idol.Armchair heroism is easy, it is true. But I know one thing: Room 101 will hold much less terror for me if I ever have to enter it, if I know then that I stood up now and spoke out while I could, leveraging what intelligence God saw fit to give me.
And that is something no boot can stamp out of existence.
US Government Agencies Are Continually Acquiring Military-Like Equipment
Facial recognition will soon end your anonymity
Nearly 250 million video surveillance cameras have been installed throughout the world, and chances are you’ve been seen by several of them today. Most people barely notice their presence anymore — on the streets, inside stores, and even within our homes. We accept the fact that we are constantly being recorded because we expect this to have virtually no impact on our lives. But this balance may soon be upended by advancements in facial recognition technology.
Soon anybody with a high-resolution camera and the right software will be able to determine your identity. That’s because several technologies are converging to make this accessible. Recognition algorithms have become far more accurate, the devices we carry can process huge amounts of data, and there’s massive databases of faces now available on social media that are tied to our real names. As facial recognition enters the mainstream, it will have serious implications for your privacy. READ MORE
Know Your Rights at Checkpoints and what Is Consent
This post is more for information and solidarity than for anything else as a foreigner commenting on these issues, but for those who are not aware of their own rights at checkpoints here is a brief primer.The key principles here are RIGHTS and CONSENT.
Remain CALM and KNOW your RIGHTS.
Hope it helps and the Forces of Darkness are lifted from Amerika and the rest of the world so we can all live in peace and freedom.
The CONSENT is not a small thing because when we give them our CONSENT they can use it to do anything and everything they can get away it. The slippery slope BEGINS and ENDS with CONSENT.

THE FOUNDATION FREEDOM CARD
The U.S. Constitution prohibits the government from interfering with your right to remain silent, to consult with an attorney, and to be free from unreasonable searches and seizures by law enforcement. However, it is up to you to assert these rights. This NORML Foundation Freedom Card will help you do so effectively. If you are confronted by a police officer, remain calm. Be Courteous and provide your identification. Politely refuse to answer any further questions. Ask to talk to an attorney. Do not consent to any search of your person, your property, your residence or your vehicle. Tell the officer you would
Like to give him or her card, which is a statement of the constitutional rights you wish to invoke. Do not reach for this card until you have obtained the officer’s permission to do so.
What to say to police if stopped;
I hereby invoke and refuse to waive all of the following rights and Privileges afforded to me by the U.S. Constitution:
• I invoke and refuse to waive my Fifth Amendment right to remain silent. Do not ask me any questions.
• I invoke and refuse to waive my Sixth Amendment right to an Attorney of my choice. Do not ask me any questions without my Attorney present.
• I invoke and refuse to waive all privileges and rights pursuant to the case Miranda v. Arizona. Do not ask me any questions or make any comment to me about this decision.
• I invoke and refuse to waive my Fourth Amendment right to be free from unreasonable searches and seizures. I do not consent to any search or seizure of myself, my home, or of any property in my possession. Do not ask me about my ownership interest in any property. I do not consent to this contact with you. If I am not presently under arrest or under investigatory detention, please allow me to leave.
• Any statement I make, or alleged consent I give, in response to your questions is hereby made under protest and under duress and in submission to your claim of lawful authority to force me to provide you with information.
DHS Creates Compromised Communities to Implement Martial Law
This Huge Camera Rig Busts People for Texting and Driving
If you live in British Columbia, don’t try to
sneak out a quick text while driving just because you don’t see any cops
on the road. The RCMP., Canada’s version of the FBI, have started using
DLSR cameras attached to massive scopes to spot distracted drivers from as far as three-quarters-of-a-mile away.
We all instinctively know to hide our phones while driving when we
see a police car, but that doesn’t make using them any less illegal.
(And it’s incredibly dangerous too, by the way.) To catch drivers in the
act, traffic services in British Columbia have been using spotting
scopes—which feature a distinctive bend to make them more comfortable to
use—for years now. Now the police are adding a 24.2-megapixel DSLR to
the rig to capture photos of the illegal act.RCMP isn’t saying where the spotting scopes are being set up for obvious reasons, but it has admitted they are primarily being used at intersections t which drivers are stopped at a red light or a stop sign—where it’s still illegal to use your phone. It’s also easier for officers to snap a sharp photo of the offense when a vehicle isn’t whizzing by.
Facial profiling: Israeli start-up says its tech can detect terrorists from just looking at a face
Israeli start-up Faception is claiming it can spot terrorists by
simply analyzing their faces and says it is working with “a leading
Homeland Security Agency” to identify potential threats.
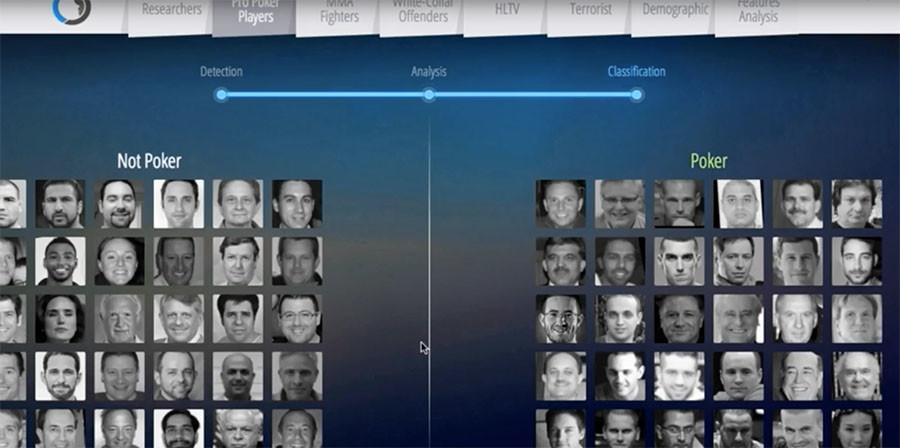
The company, founded in 2014, uses “computer vision and machine learning technology” to profile people from just a facial image and says it can reveal a range of personality traits and types.So far it has built 15 different classifiers, including extrovert, genius, academic researcher, professional poker players, bingo player, brand promoter, white collar offender, paedophile and terrorist. However Faception notes on its website that this is customizable and a relevant classifier could be built if the desired behaviour originates from a person’s DNA.
DNA is the key, according to company CEO Shai Gilboa. “Our personality is determined by our DNA and reflected in our face. It’s a kind of signal,” he told The Washington Post.
The company also relies on ‘social and life science research’ to back up its considerable claim, citing research from Edinburgh University exploring the impact genetics has on personality traits by studying identical and non-identical twins
Homeland security and public safety are the primary focus of Faception, although the technology is also applicable to financial services, marketing and artificial intelligence.

“Only three of the 11 terrorists had a previous record, our technology classified nine of those as potential terrorists with no prior knowledge, that’s why we’re working with the leading Homeland Security Agency,” the video claims.
It also noted its success at a poker tournament where two of the four players it predicted as the best out of 50 made it into the final. It compared the photos of the amateur players against a Faception database of professional poker players to get those results.
The practice has echoes of phrenology, a long debunked, 19th-century pseudoscience based on the theory that personality traits could be predicted by measurements of the skull and used to justify racism in its time.
Experts are also questioning the ethical implications of the practice and if it is merely pseudoscience computerized.
“The evidence that there is accuracy in these judgments is extremely weak,” Alexander Todorov, a Princeton psychology professor whose research includes facial perception told The Washington Post. “Just when we thought that physiognomy ended 100 years ago. Oh, well.”
Mosquito Drones Ready To Make Appearance
People fear robots are becoming too human, but, in reality, robots are becoming a little more bug-like every day. A team of Harvard University researchers proved this axiom when they found the solution to extending tiny robot flight is by mimicking the way small bugs alight on walls and ceilings.
The applications for such a robot are wide-ranging, from small spying devices that can conduct surveillance missions while suspended from a ceiling to research drones that can allow scientists to take measurements where no other sensors can physically go. READ MORE
GOOGLE: Conceived, Funded and Directed By the CIA
How the CIA made Google
.
Inside the secret network behind mass surveillance, endless war, and Skynet—
Part 1
By Nafeez Ahmed_______________________________________________________________________
INSURGE INTELLIGENCE, a new crowd-funded investigative journalism project, breaks the exclusive story of how the United States intelligence community funded, nurtured and incubated Google as part of a drive to dominate the world through control of information. Seed-funded by the NSA and CIA, Google was merely the first among a plethora of private sector start-ups co-opted by US intelligence to retain ‘information superiority.’
_______________________________________________________________________
The origins of this ingenious strategy trace back to a secret Pentagon-sponsored group, that for the last two decades has functioned as a bridge between the US government and elites across the business, industry, finance, corporate, and media sectors. The group has allowed some of the most powerful special interests in corporate America to systematically circumvent democratic accountability and the rule of law to influence government policies, as well as public opinion in the US and around the world. The results have been catastrophic: NSA mass surveillance, a permanent state of global war, and a new initiative to transform the US military into Skynet.
This exclusive is being released for free in the public interest, and was enabled by crowdfunding. I’d like to thank my amazing community of patrons for their support, which gave me the opportunity to work on this in-depth investigation. Please support independent, investigative journalism for the global commons.
In the wake of the Charlie Hebdo attacks in Paris, western governments are moving fast to legitimize expanded powers of mass surveillance and controls on the internet, all in the name of fighting terrorism.
US and European politicians have called to protect NSA-style snooping, and to advance the capacity to intrude on internet privacy by outlawing encryption. One idea is to establish a telecoms partnership that would unilaterally delete content deemed to “fuel hatred and violence” in situations considered “appropriate.” Heated discussions are going on at government and parliamentary level to explore cracking down on lawyer-client confidentiality.
What any of this would have done to prevent the Charlie Hebdo attacks remains a mystery, especially given that we already know the terrorists were on the radar of French intelligence for up to a decade.
There is little new in this story. The 9/11 atrocity was the first of many terrorist attacks, each succeeded by the dramatic extension of draconian state powers at the expense of civil liberties, backed up with the projection of military force in regions identified as hotspots harbouring terrorists. Yet there is little indication that this tried and tested formula has done anything to reduce the danger. If anything, we appear to be locked into a deepening cycle of violence with no clear end in sight.
As our governments push to increase their powers, INSURGE INTELLIGENCE can now reveal the vast extent to which the US intelligence community is implicated in nurturing the web platforms we know today, for the precise purpose of utilizing the technology as a mechanism to fight global ‘information war’ — a war to legitimize the power of the few over the rest of us. The lynchpin of this story is the corporation that in many ways defines the 21st century with its unobtrusive omnipresence: Google.
Google styles itself as a friendly, funky, user-friendly tech firm that rose to prominence through a combination of skill, luck, and genuine innovation. This is true. But it is a mere fragment of the story. In reality, Google is a smokescreen behind which lurks the US military-industrial complex.
The inside story of Google’s rise, revealed here for the first time, opens a can of worms that goes far beyond Google, unexpectedly shining a light on the existence of a parasitical network driving the evolution of the US national security apparatus, and profiting obscenely from its operation.
The shadow network
For the last two decades, US foreign and intelligence strategies have resulted in a global ‘war on terror’ consisting of prolonged military invasions in the Muslim world and comprehensive surveillance of civilian populations. These strategies have been incubated, if not dictated, by a secret network inside and beyond the Pentagon.Established under the Clinton administration, consolidated under Bush, and firmly entrenched under Obama, this bipartisan network of mostly neoconservative ideologues sealed its dominion inside the US Department of Defense (DoD) by the dawn of 2015, through the operation of an obscure corporate entity outside the Pentagon, but run by the Pentagon.
In 1999, the CIA created its own venture capital investment firm, In-Q-Tel, to fund promising start-ups that might create technologies useful for intelligence agencies. But the inspiration for In-Q-Tel came earlier, when the Pentagon set up its own private sector outfit.
Known as the ‘Highlands Forum,’ this private network has operated as a bridge between the Pentagon and powerful American elites outside the military since the mid-1990s. Despite changes in civilian administrations, the network around the Highlands Forum has become increasingly successful in dominating US defense policy.
Giant defense contractors like Booz Allen Hamilton and Science Applications International Corporation are sometimes referred to as the ‘shadow intelligence community’ due to the revolving doors between them and government, and their capacity to simultaneously influence and profit from defense policy. But while these contractors compete for power and money, they also collaborate where it counts. The Highlands Forum has for 20 years provided an off the record space for some of the most prominent members of the shadow intelligence community to convene with senior US government officials, alongside other leaders in relevant industries.
I first stumbled upon the existence of this network in November 2014, when I reported for VICE’s Motherboard that US defense secretary Chuck Hagel’s newly announced ‘Defense Innovation Initiative’ was really about building Skynet — or something like it, essentially to dominate an emerging era of automated robotic warfare.
That story was based on a little-known Pentagon-funded ‘white paper’ published two months earlier by the National Defense University (NDU) in Washington DC, a leading US military-run institution that, among other things, generates research to develop US defense policy at the highest levels. The white paper clarified the thinking behind the new initiative, and the revolutionary scientific and technological developments it hoped to capitalize on.
The Highlands Forum
The co-author of that NDU white paper is Linton Wells, a 51-year veteran US defense official who served in the Bush administration as the Pentagon’s chief information officer, overseeing the National Security Agency (NSA) and other spy agencies. He still holds active top-secret security clearances, and according to a report by Government Executive magazine in 2006 he chaired the ‘Highlands Forum’, founded by the Pentagon in 1994.
New Scientist magazine (paywall) has compared the Highlands Forum to elite meetings like “Davos, Ditchley and Aspen,” describing it as “far less well known, yet… arguably just as influential a talking shop.” Regular Forum meetings bring together “innovative people to consider interactions between policy and technology. Its biggest successes have been in the development of high-tech network-based warfare.”
Given Wells’ role in such a Forum, perhaps it was not surprising that his defense transformation white paper was able to have such a profound impact on actual Pentagon policy. But if that was the case, why had no one noticed?
Despite being sponsored by the Pentagon, I could find no official page on the DoD website about the Forum. Active and former US military and intelligence sources had never heard of it, and neither did national security journalists. I was baffled.
The Pentagon’s intellectual capital venture firm
In the prologue to his 2007 book, A Crowd of One: The Future of Individual Identity, John Clippinger, an MIT scientist of the Media Lab Human Dynamics Group, described how he participated in a “Highlands Forum” gathering, an “invitation-only meeting funded by the Department of Defense and chaired by the assistant for networks and information integration.” This was a senior DoD post overseeing operations and policies for the Pentagon’s most powerful spy agencies including the NSA, the Defense Intelligence Agency (DIA), among others. Starting from 2003, the position was transitioned into what is now the undersecretary of defense for intelligence. The Highlands Forum, Clippinger wrote, was founded by a retired US Navy captain named Dick O’Neill. Delegates include senior US military officials across numerous agencies and divisions — “captains, rear admirals, generals, colonels, majors and commanders” as well as “members of the DoD leadership.”What at first appeared to be the Forum’s main website describes Highlands as “an informal cross-disciplinary network sponsored by Federal Government,” focusing on “information, science and technology.” Explanation is sparse, beyond a single ‘Department of Defense’ logo.
But Highlands also has another website describing itself as an “intellectual capital venture firm” with “extensive experience assisting corporations, organizations, and government leaders.” The firm provides a “wide range of services, including: strategic planning, scenario creation and gaming for expanding global markets,” as well as “working with clients to build strategies for execution.” ‘The Highlands Group Inc.,’ the website says, organizes a whole range of Forums on these issue.
For instance, in addition to the Highlands Forum, since 9/11 the Group runs the ‘Island Forum,’ an international event held in association with Singapore’s Ministry of Defense, which O’Neill oversees as “lead consultant.” The Singapore Ministry of Defense website describes the Island Forum as “patterned after the Highlands Forum organized for the US Department of Defense.” Documents leaked by NSA whistleblower Edward Snowden confirmed that Singapore played a key role in permitting the US and Australia to tap undersea cables to spy on Asian powers like Indonesia and Malaysia.
The Highlands Group website also reveals that Highlands is partnered with one of the most powerful defense contractors in the United States. Highlands is “supported by a network of companies and independent researchers,” including “our Highlands Forum partners for the past ten years at SAIC; and the vast Highlands network of participants in the Highlands Forum.”
Continue reading HERE.








